Hamza bin Dlaj family denied rumors that promote social networking sites related to the decision of his execution, along with it many of the media reaction to the pages of Facebook.It is reported that a young Algerian Hamza bin Dlaj and who made the event in newspapers and US media, this is the culprit according to investigators, the FBI FBI statements made cybersquatting on 217 Bank Loyalty to dozens of Malaysian banks ..butroh Capacity in $ 3.4 billion and that the weakest the proceeds of the robbery was coming out where Hamza $ 10 million.Hamza, who is married to a Malaysian girl located by investigators in London, was arrested in Bangkok Thailand airport anyone coming from Malaysia and headed then to Cairo via flight from Bangkok to Cairo and from the access to the Algerian territory and stealthy hiding after learning as a follow up by the FBIHamza and used on the move 17 passport and his image but under a pseudonym and has passports of several countries addition to its use in its operations, extraordinary devices based where the two phones iPhone 4 and a phone Qalaaksa Samsnog equipped contact with the satellite and computer also connected to a satellite and some Alogisellat loaded on his computer and credit cards virgin pseudonyms and Bkudat complex used in the conversion of the stolen money to it .Algerian young man visited more than 100 countries in 3 years and live in Malaysia, where it is said to have helped dozens of Algerians was physically and pay guarantees in order to bring out the Algerians locked in Malaysia
jeudi 20 août 2015
Do really were sentenced to death on the Algerian hackers smiling "Hamza bin Dlaj"?
Hamza bin Dlaj family denied rumors that promote social networking sites related to the decision of his execution, along with it many of the media reaction to the pages of Facebook.It is reported that a young Algerian Hamza bin Dlaj and who made the event in newspapers and US media, this is the culprit according to investigators, the FBI FBI statements made cybersquatting on 217 Bank Loyalty to dozens of Malaysian banks ..butroh Capacity in $ 3.4 billion and that the weakest the proceeds of the robbery was coming out where Hamza $ 10 million.Hamza, who is married to a Malaysian girl located by investigators in London, was arrested in Bangkok Thailand airport anyone coming from Malaysia and headed then to Cairo via flight from Bangkok to Cairo and from the access to the Algerian territory and stealthy hiding after learning as a follow up by the FBIHamza and used on the move 17 passport and his image but under a pseudonym and has passports of several countries addition to its use in its operations, extraordinary devices based where the two phones iPhone 4 and a phone Qalaaksa Samsnog equipped contact with the satellite and computer also connected to a satellite and some Alogisellat loaded on his computer and credit cards virgin pseudonyms and Bkudat complex used in the conversion of the stolen money to it .Algerian young man visited more than 100 countries in 3 years and live in Malaysia, where it is said to have helped dozens of Algerians was physically and pay guarantees in order to bring out the Algerians locked in Malaysia
mardi 18 août 2015
Android 6.0 Marshmallow is the next version of Google's mobile software
Google has made it a thing to name its Android OS versions
This version, which has been called “M” until now, had its name unveiled today….
The new “marshmallow” statue was unveiled today on Google’s campus in Mountain View.
Here’s history of Android names:
 – Alpha
– Alpha
– Beta
– Cupcake
– Donut
– Eclair
– Froyo
– Gingerbread
– Honeycomb
– Ice Cream Sandwich
– Jelly Bean
– KitKat
– Lollipop
– Marshmallow
This version, which has been called “M” until now, had its name unveiled today….
The new “marshmallow” statue was unveiled today on Google’s campus in Mountain View.
Here’s history of Android names:
 – Alpha
– Alpha– Beta
– Cupcake
– Donut
– Eclair
– Froyo
– Gingerbread
– Honeycomb
– Ice Cream Sandwich
– Jelly Bean
– KitKat
– Lollipop
– Marshmallow
By:
DT-TECH
dimanche 26 juillet 2015
10 Best Hacking Tools for windows
1.Nmap
Nmap is otherwise called the Swiss armed force blade of hacking. It is the best port scanner with a great deal of capacities In hacking, Nmap is typically utilized as a part of the foot printing stage to check the ports of the remote PC to figure out wich ports are open.
Download
2.Wire shark
Wire shark is a bundle sniffer. It catches all system activity experiencing a system connector. At the point when perforing man in the center assaults utilizing devices like Cain, we can utilize Wire shark to catch the activity and break down it for succulent information like usernames and passwords. It is utilized by system heads to perform system investigating.
Download
3.Cain and Able
Cain and Abel is a multipurpose windows just hacking device. It is a touch old now, yet despite everything it does the occupation well. Cain can be utilized to break windows secret key, perform man in the center assaults, catch system passwords and so on.
Download
4.Metasploit
Metasploit is an immense database of adventures. There are a huge number of adventure codes, payloads that can be utilized to assault web servers or any PC so far as that is concerned. This is a definitive hacking instrument that will permit you to really "hack" a PC. You will have the capacity to get root access to the remote PC and plant secondary passages or do some other stuff. It is best to utilize metasploit under Linux
Download
5.Aircrack-ng
Aircrack-ng is a situated of apparatuses that are utilized to break wifi passwords. Utilizing a blend of the devices in aircrack, you can without much of a stretch split WEP passwords. WPA passwords can be broken utilizing word reference or savage power. Despite the fact that aircrack-ng is accessible for Windows, it is best to utilize it under Linux environment. There are numerous issues on the off chance that you utilize it under Windows environment.
Download
6.Nessus
Nessus is a comprehensive automatic vulnerability scanner. You have to give it an IP address as input and it will scan that IP address to find out the vulnerabilities in that system. Once you know the vulnerabllities, you can use metasploit to exploit the vulnerablity. Nessus works both in Windows and Linux.
Download
7.Netcat
Netcat is an extraordinary systems administration utility which peruses and composes information crosswise over system associations, utilizing the TCP/IP convention. It is otherwise called the swiss armed force blade for TCP/IP. This is on account of netcat is to a great degree flexible and can perform verging on anything identified with TCP/IP. In a hacking situation, it can be utilized as a secondary passage to get to hacked PCs remotely. The utilization of netcat is constrained just by the client's creative energy. Discover all the more about netcat at the official site.
Download
By:
DT-TECH
mardi 14 juillet 2015
Mozilla has blocked all versions of Flash from running in Firefox again
Firefox users now automatically protected from that dastardly new Flash bug that was stolen and weaponized recently. Mozilla decided that the best way to keep its users safe was to stop the Flash plugin from running. At least for now. It’s not the Flashpocalypse that some bloggers are making it out to be. Mozilla did not, in fact, “take Flash out behind the shed” and put a bullet in it.
The truth is that this was business as usual for Mozilla. They’ve blocked problematic plugins — like Java, for example — before. It’s all part of Mozilla’s security strategy. Sometimes, they say, security of the Firefox user base has to be prioritized over a seamless web experience. That’s exactly what happened this week. A couple of high-severity Flash bugs were reported. One was stolen by hackers who infiltrated the “security” firm Hacking Team and then weaponized in short order by cybercriminals. Another popped up a few days later that affected all version of Flash, including the latest, 18.0.0.209.
Hit a page that uses Flash right now with Firefox and you’ll probably see the result: a warning like the one at the top of this post. Then again, you might not see it.
If you’ve browsed Mozilla’s support docs before, you may have stumbled across one of their proposed remediations for Flash security issues: remove it. You can probably get along just fine without it, if not permanently at least until Adobe squashes this latest critical bug.
One day soon, hopefully, Mozilla’s Shumway project will come to fruition and you’ll be able to run Flash content without the need for Adobe’s plugin. That day can’t come soon enough, and when it does, then headlines about Mozilla putting Flash out its misery (or putting us out of Flash’s misery) will actually be true.
By:
DT-TECH
mercredi 8 juillet 2015
Kali linux 2.0 coming August 11th 2015
Ever since its debut in the year 2013, Kali Linux users were waiting for a new and revamped version of the hack-friendly OS. Now Kali Linux developers announced the next version-Kali Sana.
This popular hacking and penetration testing platform will release Kali Linux 2.0, codenamed Kali Sana, on August 11, 2015. Kali Linux has been a widely successful system developed by Offensive Security through the rewrite of BackTrack, another forensics Linux distribution.The team working on Kali Linux 2.0 says that the new platform is full of the most powerful features for digital forensics. The next version will be showcased at the DEF CON hacking confab in August.
- The core set tools in Kali will be weekly updated.
- Kali UI is redesigned for a streamlined working environment.
- Native support for Ruby 2.0 for faster Metasploit load times.
- Built in screencasting and desktop notifications.
- Cutting-edge wireless penetration tools and more.

By:
DT-TECH
samedi 4 juillet 2015
How To Make Simple Calculator in C programming
This is a code made in c program
.This program takes an arithmetic operator (+, -, *, /)
Here copy the given code below and paste it in your c program software,
Here copy the given code below and paste it in your c program software,
/* Source code to create a simple calculator for addition, subtraction, multiplication and division in C programming. */
# include
int main()
{
char o;
float num1,num2;
printf("Enter operator either + or - or * or divide : ");
scanf("%c",&o);
printf("Enter two operands: ");
scanf("%f%f",&num1,&num2);
switch(o) {
case '+':
printf("%.1f + %.1f = %.1f",num1, num2, num1+num2);
break;
case '-':
printf("%.1f - %.1f = %.1f",num1, num2, num1-num2);
break;
case '*':
printf("%.1f * %.1f = %.1f",num1, num2, num1*num2);
break;
case '/':
printf("%.1f / %.1f = %.1f",num1, num2, num1/num2);
break;
default:
/* If operator is other than +, -, * or /, error message is shown */
printf("Error! operator is not correct");
break;
}
return 0;
}
By:
DT-TECH
mercredi 1 juillet 2015
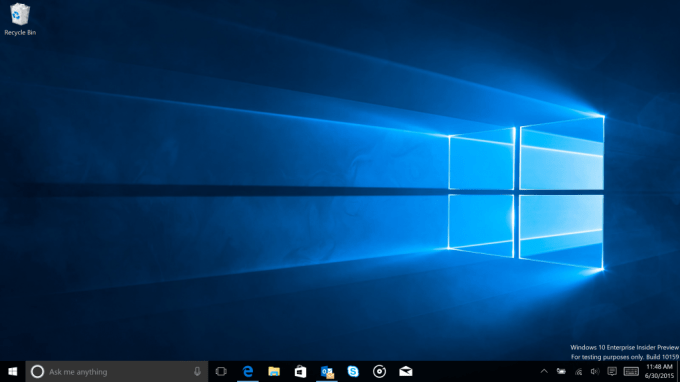
Microsoft released another Windows 10 contains a new desktop background
the operating system iteration contains a new desktop background. It appears to be the image that Microsoft will use as Windows 10’s default shot.
By:
DT-TECH
Inscription à :
Commentaires (Atom)